It is an undeniable fact that companies are consistently engaged in a battle against cybercriminals by enhancing their cyber defenses. This race has no end and the businesses have no other option except to stay ahead of the criminals. To safeguard their interests effectively, organizations must enhance their security by striking a balance between defensive, detection, and responsive measures. The is especially true in light of the rapid emergence and evolution of modern fraud schemes.
As cybercrime becomes increasingly sophisticated, organizations must acknowledge this – they are not only involved in a war with these cyber criminals but there is no “one-time” winning in this battle. This battle demands constant effort and strategic thinking.
The importance and effects of cybersecurity on the global business agenda remain unchanged. No industry can be immune to these threats, but financial institutions remain an attractive target.
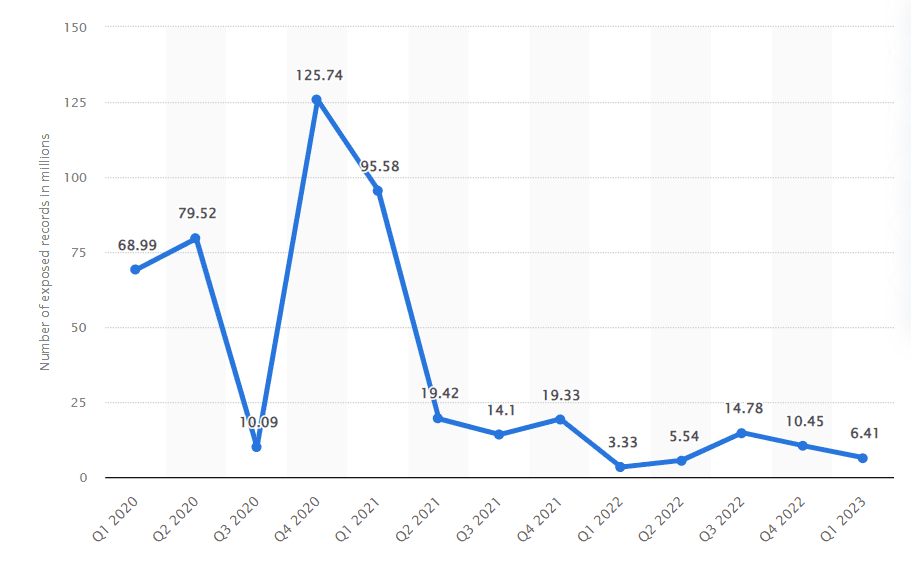
Data: Statista – Number of data records exposed worldwide
The repercussions of these cyber-attacks and fraud schemes can be brutal, affecting both financial stability and reputation, representing a threat to your business and customers. Remember that the CEO or business owner is held responsible for any failures and is expected to shoulder this heavy responsibility on multiple fronts. Therefore, they must stay informed and be well prepared with their tech team. They are required to actively work to reduce risks to stay ahead and function safely.
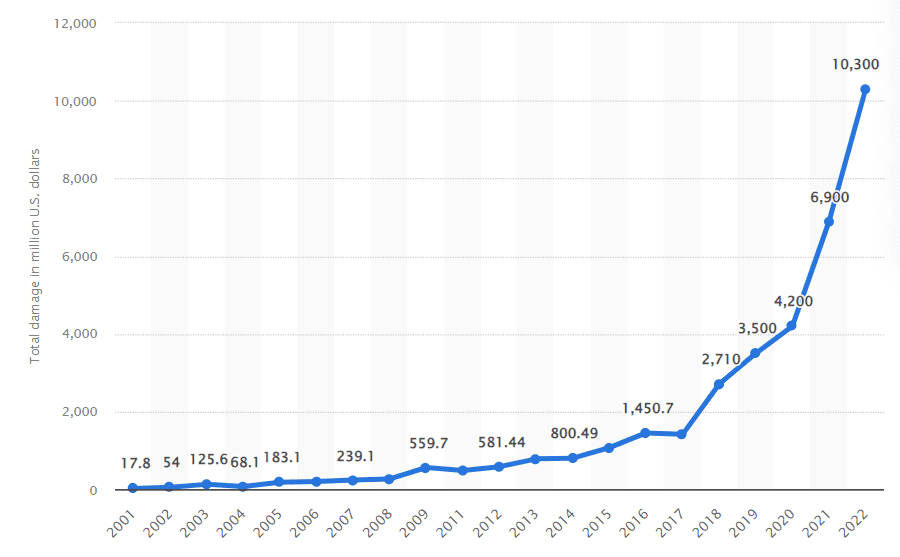
Data: Statista – Annual amount of monetary damage by cybercrime in the US
What Is Cyber Defense?
Cyber defense refers to the measures taken to protect against attacks on computer or server networks. It involves safeguarding critical infrastructure and ensuring client information security for various corporations and government bodies. It is equally important for many startups and entrepreneurs in the modern-day threat environment.
The main focus of cyber defense is to predict, detect, prevent, and respond promptly to these attacks. This ensures the integrity of the business security infrastructure. As cyber threats become more common, complex, and pervasive, the importance of cyber defense has grown significantly. It is crucial to safeguard sensitive data and preserve valuable assets.
The Origins of Cyber Attacks
Cyberattacks originate from different sources with different motives and different scales. Here are some common ones:
1- Unpredictable Hackers
Initially, cyber threats were posed by opportunistic individuals who created multiple cyber threats and tried to get access to personal data or information with the primary goal of personal amusement and recognition. Your organization can be an easy target of these “unpredictable hackers” if your business lacks proper security measures.
2- Sophisticated Hackers
With the mainstream adoption of computing came the rise of “hackers.” While some seek financial gain, many are motivated by social, political, and environmental causes. Today, these attackers have grown in sophistication and may target organizations based on ideological differences.
3- Organized Attackers
In the early 21st century, traditional criminals recognized the power of cybercrime, starting with scams like phishing or spyware threats. This criminal landscape has become an organized, intricate ecosystem where cyber tools, techniques, and stolen data are traded extensively.
Organized crimes can include a wide range of activities involving sophisticated data theft, ransomware, denial-of-service attacks, and intellectual property theft. Recently, attackers have also focused on attacking individuals by cheating people to undermine organizations’ safety instead of solely relying on breaching complex shields and protections.
4- Business Espionage
Industrial spies transitioned to the virtual world as businesses moved their operations online. Corrupt insiders or external rivals frequently carry out these espionage actions. Their techniques have grown more advanced and evolving interconnected technology.
The landscape of cyber threats has expanded and evolved, necessitating robust cybersecurity measures to counter these diverse sources of attacks.
Emerging Threats and Modern Cybersecurity
Nowadays, malicious actors are employing increasingly sophisticated tactics, utilizing tools like generative artificial intelligence (AI) to revamp behavior-driven scams. This poses a growing threat to a company’s security defenses and impacts its customer loyalty.

In the payment industry, the challenge lies in traditional security measures, reliant on rule-based engines. This often creates friction for Gen-Z type of modern consumers who expect seamless payment experiences. These consumers, value convenience and efficiency in their interactions.
To address this evolving threat landscape, businesses must adopt cybersecurity strategies that detect and prevent fraud and offer real-time authentication and verification of consumers’ digital identities. This approach safeguards against account takeovers while seamlessly accommodating any necessary updates or changes. In our modern society, the value of digital identities is increasing, and they are becoming equally important as physical driver’s licenses or passports.
As our world becomes increasingly digital, cybercriminals are seizing countless opportunities to exploit the vast amount of data available. This allows them to create artificial identities known as synthetic personas. With these fake identities, they are easily able to propagate new fraud schemes to the vulnerable lot. This raises the stakes for businesses to implement effective yet secure authentication processes.
Businesses must leverage advanced strategies and solutions to defend against cyber attacks successfully. These solutions should combine technology and data analytics. Educating and training their employees should be an integral part of their system.
An orchestrated approach that integrates these elements is critical to protecting the organization and its valued customers in this era of heightened cybersecurity challenges.
How Could AI Be the Solution to Cybersecurity Going Ahead?

● Threat Hunting:
Traditional security methods rely on known signatures or indicators of compromise to identify threats. While effective against familiar threats, they must improve when dealing with undiscovered ones. Signature-based techniques can catch around 90% of threats, but integrating with AI can boost detection rates to 95%.
A more effective approach is to combine traditional methods with AI, achieving a 100% detection rate while minimizing false alarms. AI can also enhance threat hunting by incorporating behavioral analysis, such as using AI models to create profiles of every application within an organization’s network based on extensive endpoint data processing.
● Vulnerability Management:
The ever-increasing number of reported vulnerabilities poses a challenge for organizations. Traditional ways of security react only when they detect high-risk vulnerabilities. AI and modern techniques like User and Event Behavioral Analytics (UEBA) analyze the baseline behavior of user accounts, endpoints, and servers to identify abnormal patterns.
This proactive approach helps protect organizations even before vulnerabilities are officially reported and patched.
● Data Centers:
AI’s capabilities extend to optimizing and monitoring critical data center processes, such as backup power, cooling systems, power consumption, temperature regulation, and bandwidth usage.
By continuously monitoring and providing data-driven insights, AI enhances the efficiency and security of hardware and infrastructure. Furthermore, AI can reduce hardware maintenance costs by providing early alerts for necessary repairs, as demonstrated by Google’s success in lowering cooling costs and power consumption within their data centers.
● Network Security:
Traditional network security involves labor-intensive tasks like creating security policies and understanding network topography. It is important to accurately identify the relation between workloads and applications. Although this can be time-consuming if done with traditional methods. AI can help reduce time, resources, and cost.
AI can learn network traffic patterns and recommend functional grouping of workloads and security policies, streamlining these critical aspects of network security.
Tips For Protecting Your Business From Cyber Threats – Cybersecurity Best Practices
Besides AI integration, businesses must have adequate strategies for different security-related scenarios. Proactively preventing cyberattacks is the most effective strategy for safeguarding your organization’s information. Here are some practical tips to enhance your organization’s network security:
Employee Education: Start by educating your employees about the significance of cybersecurity and the potential risks associated with cyberattacks. Ensure they have a solid grasp of fundamental computer security principles, such as identifying viruses and safeguarding their data. Additionally, emphasize the importance of reporting any suspicious activities or behavior promptly.
Antivirus Software: Install reliable antivirus software on all corporate PCs and servers. Keep this software up-to-date and configure it correctly to effectively identify new strains of viruses and malware.
Network Perimeter Protection: Strengthen your network’s perimeter security with robust passwords and firewalls. Ensure that all network users can create strong passwords and that their computers are isolated from other networks.
Communication Monitoring: Keep a close eye on incoming and outgoing communications. Know your customers and be aware of which employees handle orders or deals. This will enable better control over information flow.
Data Backups: Avoid centralizing sensitive information on a single PC. Regularly back up your data to a secure off-site location to mitigate data loss risks, preferably every month.
Periodic Security Testing: Use automated technologies online to do recurring internal penetration testing. These tests help identify security configuration issues, application vulnerabilities, and potential attack surfaces within your network.
Policy Implementation: Establish comprehensive policies to safeguard confidential information. Encrypt sensitive data stored on the network, require employees to provide business identification upon request for authorized access, regularly update access control passwords, and enforce strong password requirements (at least eight characters with a mix of upper and lower case letters and numbers) for all logins.
Access Control: Implement stringent access controls for your network to restrict unauthorized entry effectively.
Network Segmentation: Maintain separate wireless and wired networks in your workspace or private offices. Ensure both networks are equipped with robust security measures and access control policies.
What Does the Future Hold?
Attackers are becoming more sophisticated, employing targeted and advanced techniques. Organizations must develop equally sophisticated defenses, detection mechanisms, and response capabilities to counter these threats effectively.
Additionally, the regulatory landscape is undergoing significant changes. Data protection, safeguarding critical information, and ensuring the security of financial services are areas where regulations are tightening.
For instance, the Network Information Security Directive and EU General Data Protection Regulation released in 2018 is an important shift toward a more secure world. Companies are now compelled by law to prevent data breaches and secure their customers’ data.
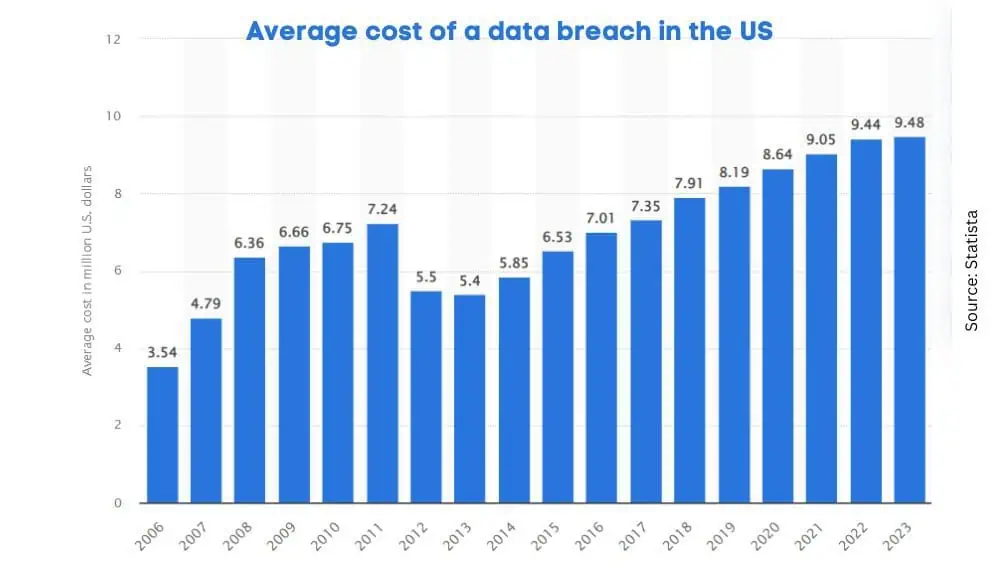
Sustained investment is also crucial to maximize the benefits of existing cybersecurity. These investments ensure that organizations can meet the ever-increasing standards for cybersecurity. To achieve this, a structured approach to cyber defense is essential.
Conclusion
Businesses must stay prepared to handle the ever-evolving cyber risks. Cyber attacks are becoming sophisticated and multi-faceted with each passing day. Big and small businesses should invest and upgrade their cyber defense to prevent such attacks. They should strictly follow the shields-up guidance provided by cyber security groups and companies from time to time.
It is important that governments too should step in and improve the cyber security standards of their nations. Government-to-government cooperation is crucial. Conferences like the Western Hemisphere Cyber Conference can help enhance the security environment of a region and deter cyber attacks on businesses and individuals alike.
Frequently Asked Questions
How does cybersecurity benefit businesses?
Companies that prioritize cybersecurity gain a competitive edge in the market. Robust security measures help them reduce the risk of cyber threats, allowing them to focus on their core strengths and maintain a competitive advantage.
What steps should businesses take to prevent cyberattacks?
To prevent cyberattacks, businesses should:
● Create data backups and encrypt sensitive information.
● Keep all security systems and software up-to-date.
● Conduct regular cybersecurity training for employees.
● Use strong and complex passwords.Who is responsible for cybersecurity within a company?
The Chief Information Officer (CIO) is crucial in ensuring cybersecurity controls are in place to mitigate risks.
What are the essential components of cybersecurity?
Cybersecurity comprises various essential elements, including:
● Application Security.
● Information Security.
● Network Security.
● Disaster Recovery Planning.


